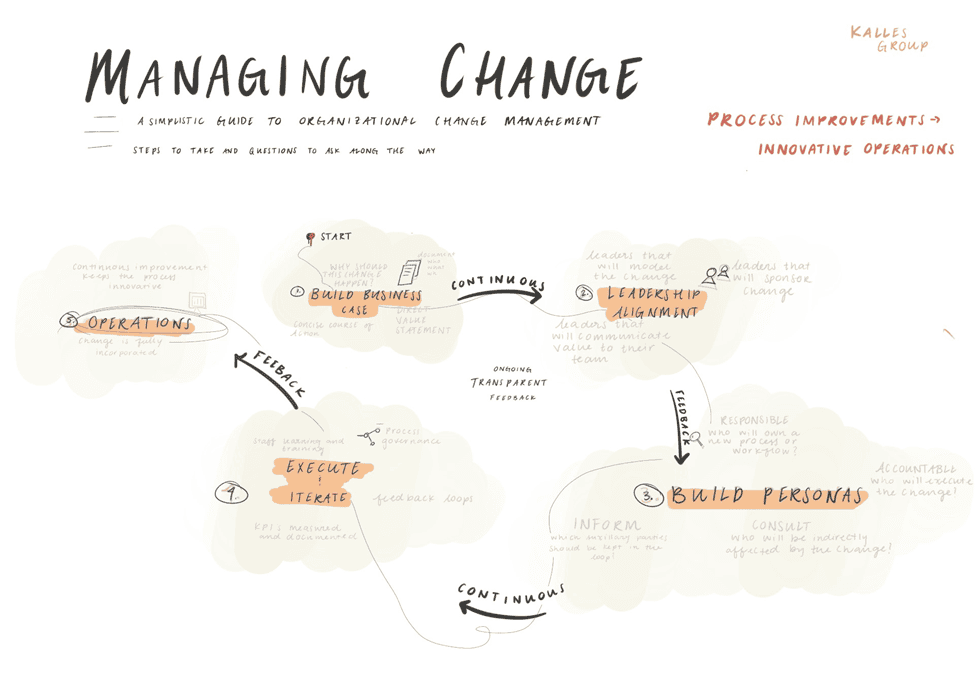
Developing a framework for operational change management
Change is an ongoing, organization-wide practice that drives innovation and competitive market placement. To constantly evolve, iterate, and adjust is to manage a competitive edge — making change a daunting yet necessary undertaking. Change management is a dexterous process. Managing change across operations requires emotional intelligence, situational awareness, data analysis, a campaigning attitude, and a […]
Developing a framework for operational change management Read More »