Why SOC 2 Compliance Really Matters
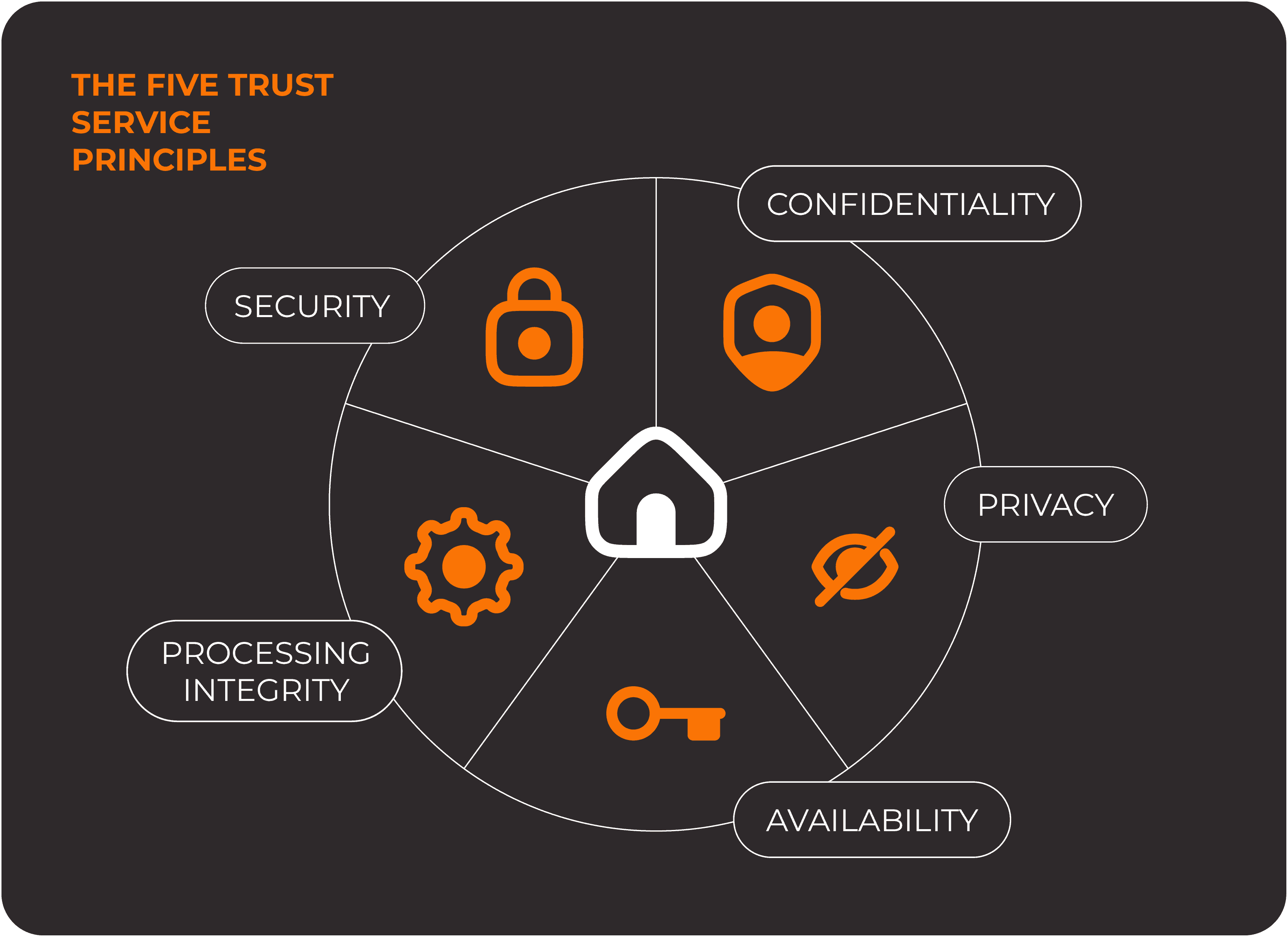
In many discussions with leaders, we hear a frequent concern: how to demonstrate data security in a way that clients find convincing. One recognized framework is SOC 2, which focuses on five trust principles—security, availability, processing integrity, confidentiality, and privacy. By following SOC 2 guidelines, you show clients that you take data governance seriously.
If your business handles sensitive data or wants to rise above rivals, SOC 2 certification is often the way to go. In some cases, SOC 1 could be relevant, but if your main worry is showing how you protect data, then SOC 2 is usually more fitting. Check out our post on security leadership development to see how a thorough approach to security can bring your leadership group together around consistent policies.
What Is the Difference Between SOC 1 and SOC 2?
The question of SOC 1 vs. SOC 2 often comes up in businesses dealing with both financial and operational controls. Here is a quick summary:
- SOC 1: Focuses on financial controls linked to financial reporting.
- SOC 2: Targets broader operational controls, mainly around data protection, privacy, and system oversight.
If your clients want proof of how you protect data and ensure system dependability, SOC 2 typically suits you best. If they care more about how your financial controls affect their statements, SOC 1 might be enough. Our example in Regulatory Expertise shows that having the right compliance can break down barriers and strengthen credibility.
Key Steps for Achieving SOC 2 Compliance
It helps to divide the SOC 2 journey into organized tasks. By following a plan and involving your staff, you can handle SOC 2 certification calmly:
- Set Your Scope: Decide which systems or services are part of SOC 2. This might include servers, cloud apps, or any tool storing client data.
- Gap Analysis: Evaluate your existing setups against your SOC 2 compliance checklist. If you notice missing logs or weak procedures, list them as targets to fix.
- Implement Fixes: Update policies, train employees about data protection, and put in place new controls such as multi-factor sign ins. Our article on secure development training shows how training can strengthen your security approach.
- Monitor Over Time: For a SOC 2 Type 2 report, you must prove your controls function well over a set period, not just on paper. This is where logs, frequent audits, and progress reviews help a lot.
- Formal Audit: An outside firm checks your evidence, interviews staff, and ensures that you meet all SOC 2 compliance requirements. Once you pass, you get a SOC 2 report to share with partners or prospects.
Building a SOC 2 Compliance Checklist
We often hear requests for a clear SOC 2 compliance checklist so teams can keep track of tasks. Here is a basic outline:
- Access Controls: Set guidelines for passwords, user roles, and quick removal of inactive accounts. Our piece on security assessments explains how to discover hidden risks.
- System Monitoring: Log system actions, watch them often, and handle any odd findings. This method used in risk remediation can also help your team see dangers more quickly.
- Incident Response: Lay out how you detect, limit, research, and note incidents. Make sure staff know who to contact if they spot trouble.
- Staff Training: Keep employees informed about secure data use. One good idea is to bring up policy points during 30 day review questions for newcomers. That way, no one is confused about the rules.
- Audit Trails: Logs and records prove your controls are operational. They also help speed up your SOC 2 audit by providing evidence that you have done what you claim.
Why Leadership Involvement Matters
Achieving SOC 2 compliance depends on engaged leaders. If top management sees compliance as optional, employees may not take it seriously. But when executives align compliance with growth or new revenue, staff pay closer attention.
A monthly discussion or a direct message from leaders about SOC 2 compliance requirements can keep the plan alive in daily routines. Our post on security leadership development shows how strong leadership fosters a culture where security is everyone’s priority.
People-First Approaches: 30 Day Review Questions
Some compliance programs fail because staff never fully understood or adopted certain controls. That is why 30 day review questions for new hires or transferring employees can help. Ask them whether they know who to talk to about data handling or if they have read the relevant policies. This makes them feel involved and ensures that they do not unknowingly break vital rules. Our SharePoint onboarding story likewise emphasizes the value of clarity for new staff.
SOC 1 vs. SOC 2: Making a Choice
When deciding SOC 1 vs. SOC 2, ask whether your primary interest is financial controls (SOC 1) or data security and privacy (SOC 2). If your clients want a deeper look at how you maintain data or system integrity, SOC 2 is likely more relevant. Our post on security compliance can also offer insights into how these frameworks complement other security measures you may already have.
Common Pitfalls and Tips
Plenty of companies stumble on the path to SOC 2 compliance:
- Staff Engagement: If employees think compliance belongs only to security teams, they might ignore it. Bring them in early, mention it at staff gatherings, and stress that each department plays a part.
- No Consistent Documentation: Even if processes exist, auditors cannot check them if they are not written down. Keep a living record of what you do.
- Weak Ongoing Oversight: Some do well for the first audit, then relax. Plan monthly or quarterly updates to see that your controls stay effective.
- Lack of Direct Business Link: If staff never see how compliance helps the organization, their motivation might fade. Tying compliance tasks to revenue or client demands can give them a sense of purpose.
Final Steps: Achieving SOC 2 Certification
When you pass the SOC 2 audit and earn a SOC 2 report, you can point to a recognized validation of your security posture. More than that, you lay a foundation that helps your team keep good habits in place for the long run. That shift from checking boxes to living compliance daily is what sets an effective program apart.
Remember, how to obtain SOC 2 compliance is about weaving security into normal operations. If you need guidance or a partner to walk with you in meeting SOC 2 compliance requirements, connect with us through our Contact Us page. We have helped many clients define their scope, train staff, and gather evidence for a SOC 2 certification that makes a real difference in winning client confidence and staff support.
By following these steps and making sure leadership and staff both value the program, you can handle your next SOC 2 audit without the usual stress. And as your organization grows, your secure and compliant environment will be ready for any new challenges that come your way.

