Cyber threat incidents continue to worsen with the adoption of remote technologies and the growing sophistication of attacks. Palo Alto Networks published a report in May 2021 indicating that attackers are getting faster at identifying and exploiting vulnerabilities immediately after they are published. The researchers observed that, between January and March 2021, adversaries began scanning for Common Vulnerabilities and Exposures (CVEs) only 15 to 60 minutes following announcements.
“It’s not just an arms race between adversaries and defenders in terms of conducting cyberattacks and protecting against them. There’s a sprint taking place as well in detecting systems with known vulnerabilities to cyberthreats,” the report says.
Threat intelligence is no longer a luxury. The changing landscape requires that threat analysts create a repeatable process that monitors for new attack types and compares them to an organization’s security capabilities. By understanding who is targeting your industry and how, you can prioritize appropriate countermeasures. Threat Intelligence is only valuable if you apply the knowledge of how attackers are targeting organizations to the next step of how attackers would likely target your environments.
Bridging the gap between threat intelligence and your controls is where many organizations fall flat. High end threat intelligence platforms automate the mapping of threat actors to indicators of compromise, but this analysis can also be performed without expensive tools.
As the industry’s standard ontology, the MITRE ATT&CK Framework helps facilitate large-scale internal and external incident analysis. ATT&CK enables threat intelligence professionals to move away from relying on indicator-driven defense models that frequently skew realistic goals and slow down response times. With MITRE ATT&CK, security leadership can make strategic decisions that maximize the impact of their security investments. However, the framework is complex and may require adaptations relevant to each organization.
This article answers the following 3 questions:
- What is the MITRE ATT&CK framework?
- What other model can help prevent and preempt cyber attacks?
- How can MITRE ATT&CK and other frameworks be adapted to best suite an organizations needs?
What is the MITRE ATT&CK framework?
MITRE ATT&CK (Adversarial Tactics, Techniques & Common Knowledge) is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, government, and the cybersecurity product and service community.
ATT&CK provides details on many actors and groups, including which techniques and tools they typically use, based on open-source reporting. The framework was introduced in 2013, funded by the National Institute of Standards and Technology (NIST).
The framework was initially centered on post-compromise detection, or an attacker’s behavior after gaining access to a network. To accommodate the need to view pre-compromise activities, MITRE added a PRE-ATT&CK domain. However, in October 2020, MITRE replaced the PRE-ATT&CK domain with two new Tactics (Reconnaissance and Resource Development).
The current ATT&CK framework structure
The current ATT&CK framework includes the following components:
- “TT” (Tactics and Techniques): A modern way of looking at cyberattacks beyond looking at the results of the attack. Tactics are the intent or reason behind an attack. Techniques are the means an adversary uses to achieve their objectives. Tactics and techniques help analysts view an attack in progress as well as indicators of compromise (IoCs).
- “CK” (Common Knowledge): Common knowledge is the documented use of tactics and techniques—an archive of procedures, commonly referred to as TTPs.
MITRE divides ATT&CK into the following matrices. Each contain various tactics and techniques associated with their subject matter. For example, Enterprise contains tactics and techniques that apply to Windows, Linux, and/or MacOS systems, while Mobile contains tactics and techniques that apply to mobile devices.
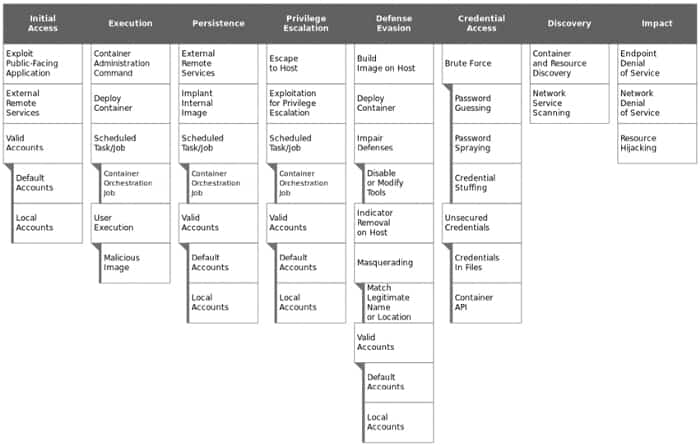
Since the framework contains such a comprehensive representation of the behaviors that attackers employ when compromising networks, it’s useful for a variety of offensive and defensive measurements, representations, and other mechanisms.
Why use MITRE ATT&CK
Mitre helps organizations truly understand adversaries and how they work. ATT&CK maps every attack phase against specific methods that attackers use to carry out the attacks. Organizations need to look at what they are trying to protect, how those resources might be attacked, and what adversaries are targeting, in order to determine which attack phases to focus on.
For instance, if a company is at an extreme risk of being targeted by ransomware groups, the company can look this up using the MITRE ATT&CK framework to see how the groups may deploy their attack. Viewing the entire attack chain gives an idea of how a ransomware attacker would move through your network, which then helps an organization focus its defense and monitoring/detection efforts.
The framework can also be used for adversary emulation and Red Teaming. Defenders can use this to simulate common adversary behavior. This can help find gaps in visibility, defensive tools, and processes.
Questions that ATT&CK can help with include:
- How effective are my defenses?
- Given limited resources, where should we prioritize spending?
- Can I detect a known adversary?
- Is the data that we collect useful?
- Evaluation of first-party and third-party tools
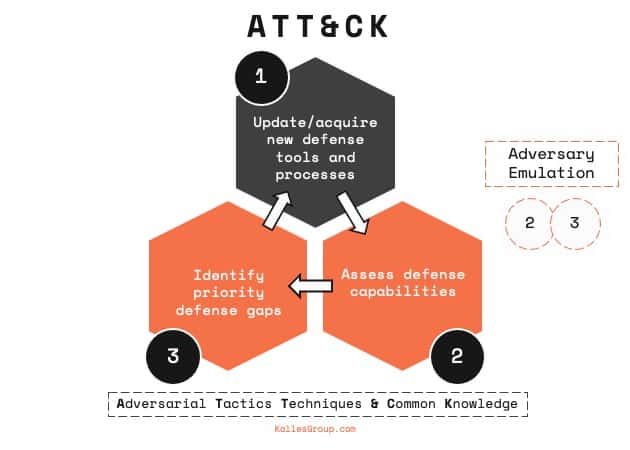
MITRE ATT&CK challenges
While MITRE ATT&CK comes with many benefits, the MITRE ATT&CK framework is also very large and complex because the data is extremely thorough. In fact, there are more than 100 different attack patterns. Mapping a company’s security infrastructure anew can be daunting and time-consuming. For that reason, defenders should be aware of other models, such as the Cyber Kill Chain Model.
What other framework can help prevent and preempt cyber attacks?
The Cyber Kill Chain model
Another popular framework that helps analyze and prevent cyber attacks is the Cyber Kill Chain Model. The Cyber Kill Chain applies the concept of the military kill chain model to a cyberattack. It’s designed for defenders to improve their defenses by analyzing an attacker’s playbook (the kill chain) and interrupting the attack by breaking the kill chain at each phase.
However, critics of the model as a threat assessment and prevention tool say the following:
- The first phases happen outside of the defended network, making it difficult to identify or defend against actions in these phases.
- The methodology is outdated because it reinforces traditional perimeter-based and malware-prevention based defensive strategies.
- It does not model insider threats well. This is especially troublesome because many of today’s attackers begin with using valid account credentials to get into the network—traffic that would not be otherwise detected as malicious.
How can the MITRE ATT&CK and other frameworks be adapted to best suite an organizations needs?
To address the limitations of the traditional kill chain and the heavy internal focus of the MITRE ATT&CK framework, a unified version of the kill chain (uniting the two frameworks) was developed in 2017 by Paul Pols in collaboration with Fox-IT and Leiden University.
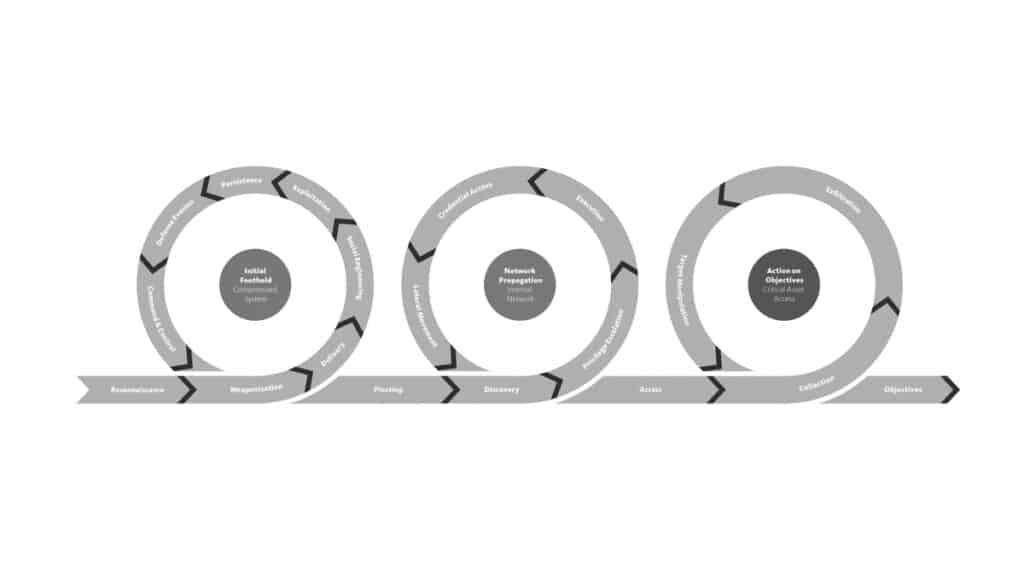
Uniting the frameworks: The Unified Kill Chain
The Unified Kill Chain provides a linear arrangement of 18 unique attack phases that may occur in end-to-end cyberattacks, covering activities that could occur outside of and within a network.
There are growing trends of ransomware-as-a-service and attacks against critical infrastructure. If an organization fits the profile of those that attackers recently targeted, the intelligence professionals could learn some of the common TTPs that ransomware groups are known for and fill the gaps in their defenses accordingly.
The three focuses of the Unified Kill Chain include:
- Initial Foothold
- Network Propagation
- Action on Objectives
Regardless of which framework an organization chooses, setting up a repeatable process for monitoring which types of attacks are happening internally (and in the larger industry) can significantly reduce the impact of future attacks.
By adapting MITRE ATT&CK, the Cyber Kill Chain Model, or similar frameworks, organizations can skillfully inform management’s decision-making processes, enhance engineering efforts, create a top-level view of the company’s security posture, and proactively protect the organization from future cyber attacks.