The holidays are over, but the cyber threats aren’t. Retail enterprises that conduct a thorough post-holiday security assessment and lock down Q1 priorities early can catch lingering vulnerabilities, prevent return-season fraud, and build a stronger security posture for the year ahead. This guide explains why cyber risk doesn’t end when holiday traffic drops, what retailers should verify now that the rush is over, and how to operationalize a simple checklist that sets your security team up for success in 2026.
Why does cyber risk persist for retailers after the holidays?
Cyber risk remains high early in the new year because attackers exploit return fraud opportunities, target exhausted security teams, leverage any weaknesses exposed during peak season, and launch tax-season phishing campaigns, all while enterprises shift focus away from security and toward inventory reconciliation and Q1 planning.
Here’s what the data shows:
- Return fraud and gift card fraud spike in January as criminals monetize stolen credentials and fake purchases from the holiday season
- Cyberattacks targeting retailers don’t pause after December; attackers analyze what worked during peak season and refine tactics for Q1
- Tax-season phishing campaigns begin ramping up in January, targeting both employees and customers with W-2 scams and fake refund offers
- Nearly half of security incidents go undetected for weeks, meaning holiday breaches may only surface now
When you combine post-holiday fatigue with a false sense of security, it creates gaps that attackers are ready to exploit.
What types of cyber threats target retailers in Q1?
Early in the new year, retailers face return fraud schemes, gift card abuse, tax-season phishing, ransomware follow-ups from holiday reconnaissance, and supply chain compromises.
The Q1 threat landscape includes:
- Return fraud and account takeover attempts using credentials stolen during holiday shopping
- Gift card draining and balance-checking bots targeting cards sold during peak season
- Tax-season W-2 and payroll phishing targeting HR and finance teams (starts in January, peaks in March-April)
- Delayed ransomware deployment from holiday-season network reconnaissance
- Supply chain and third-party compromises that went unnoticed during high-traffic periods
These campaigns target the post-holiday lull when security vigilance naturally drops, and teams are focused elsewhere.
What should retailers check now that the holidays are over?
Retail enterprises should conduct a post-holiday security assessment, validate what held up during peak season, identify gaps that emerged under pressure, and lock down Q1 priorities, including tax-season preparedness, return fraud prevention, and annual security planning.
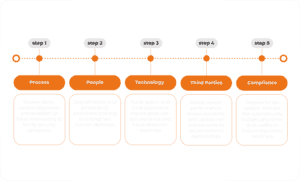
Post-Holiday Cybersecurity Assessment Checklist (Executive View)
People
- Debrief security team on holiday incidents and near-misses
- Update incident roles based on peak-season lessons learned
- Schedule Q1 security awareness training (focus: tax scams, return fraud)
Process
- Review all security alerts and anomalies from November-December
- Update incident response playbooks based on holiday experience
- Establish Q1 fraud monitoring protocols for returns and gift cards
Technology
- Audit access logs for suspicious activity during peak season
- Validate backup integrity and recovery speed after holiday load
- Review and patch any systems that showed strain during high traffic
- Tune fraud detection for return-season patterns
Third Parties
- Assess third-party vendor performance during peak season
- Review any security incidents involving payment processors or logistics partners
- Update vendor risk assessments for Q1
Compliance & Planning
- Begin tax season preparation (secure W-2 distribution, payroll system hardening)
- Allocate 2026 cybersecurity budget based on holiday findings
- Schedule annual penetration testing and compliance audits
How can retailers strengthen security posture for the year ahead without disrupting Q1 operations?
The most effective approach? Learn from what just happened, fix what broke, and build momentum for the year ahead. Focus on closing gaps exposed during peak season, preparing for tax-season threats, and setting realistic Q1 security priorities that align with business operations.
Key principles for Q1:
- Debrief thoroughly – Holiday pressure reveals what works and what doesn’t
- Fix fraud detection gaps – Return season is happening right now
- Prepare for tax season – W-2 phishing starts in January and ramps through April
- Budget strategically – Use holiday lessons to justify 2026 security investments
- Test what failed – If something struggled during peak season, don’t wait until next November to fix it
Recent studies show that organizations conducting post-incident reviews improve their security posture significantly faster than those that simply move on.
When should retailers involve external cybersecurity support for Q1?
Bring in external cybersecurity experts now if your holiday season exposed gaps your internal team can’t quickly address, if you need an objective post-mortem on what happened during peak season, or if leadership wants confidence that lessons learned translate into actual security improvements.
Common triggers:
- Security incidents occurred during the holidays, but root causes remain unclear
- Systems showed strain or failures during peak traffic
- Return fraud is spiking, and current controls aren’t catching it
- Tax season is approaching, and HR/finance systems need hardening
FAQ
Q: Is it too late to address cybersecurity issues from the holiday season?
A: No. Many breaches from November to December are only detected weeks later. Conducting a thorough assessment now can catch problems before they escalate.
Q: Should retailers prioritize new tools or process improvements in Q1?
A: Process improvements and fixing existing gaps almost always deliver faster ROI than adding new tools in Q1.
Q: What’s the biggest mistake retailers make after the holidays?
A: Assuming everything’s fine because peak season is over, when attackers are counting on that exact mindset to exploit post-holiday vulnerabilities.
Q: How is Q1 cyber risk different from holiday season risk?
A: Q1 brings return fraud, gift card abuse, tax-season phishing, and delayed impacts from holiday compromises, all while security teams are less vigilant and focused elsewhere.
Ready to close the gaps?
The vulnerabilities exposed during peak season won’t fix themselves. If you’re ready to conduct a thorough post-holiday assessment, lock down return-season fraud prevention, and build a stronger security foundation for 2026, request a free consultation with Kalles Group to assess what held up during the holidays, identify critical gaps, and build a tailored Q1 protection roadmap.
